What is Code Obfuscation and How it Works
Code obfuscation makes the applications that you create and make available to your customers and employees for use outside of your firewall more difficult to reverse engineer.
Table of Contents
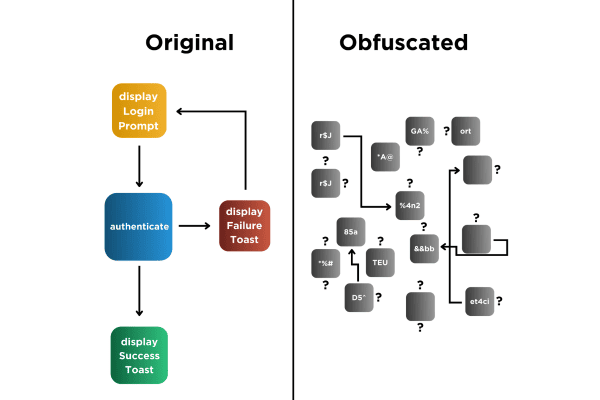
Code obfuscation is a process that makes the applications that you create for use outside of your firewall more difficult to understand after they have been decompiled or reverse engineered.
Why is Code Obfuscation Needed?
The applications you create for your employees and customers – applications that are used outside of your firewall – contain working examples that show how to access your back-end systems. They have to contain those working examples in order to work. If you do not obfuscate the code in your applications, then threat actors will be able to read that working example by simply downloading your app from the app/play or 3rd party app store, putting them in any one of the many freely available dynamic instrumentation toolkits or decompilers, and just reading the code. Code obfuscation makes this kind of subterfuge more difficult for threat actors to perpetrate.
Techniques Used In Code Obfuscation
Layout Obfuscation
Layout Obfuscation refers to a specific technique within the realm of code obfuscation aimed at protecting software by altering the structure and layout of its executable code. This method involves rearranging the order of instructions and inserting non-functional code to confuse and mislead anyone attempting to reverse engineer or analyze the software. By disrupting the logical flow that is typically expected in the code’s structure, layout obfuscation makes it significantly harder for malicious actors to discern the program’s true purpose or extract valuable data.
Data Obfuscation
Data Obfuscation is a security technique used to protect sensitive information by deliberately obscuring it to prevent unauthorized access during software development and deployment. This method involves modifying the actual data in a way that it remains usable for processing and testing, but becomes unintelligible or meaningless outside its intended context. Common techniques include masking, tokenization, and data scrambling.
Control Flow Obfuscation
Control Flow Obfuscation is an advanced code protection technique used to secure software by making its execution logic more complex and harder to understand. This method involves altering the normal, predictable execution paths of a program without changing its final output. Techniques used include inserting conditional, iterative, and jump statements that lead to misleading execution sequences and dead code paths. These interventions complicate the control flow graph of the application, making it challenging for reverse engineers or automated tools to trace the true functionality of the code or to perform static analysis.
Preventive Obfuscation
Preventive Obfuscation is a proactive security strategy that involves the use of obfuscation techniques to safeguard software code before it becomes a target of malicious activities. This approach anticipates potential security threats and implements obfuscation methods such as layout, data, and control flow obfuscation early in the software development lifecycle. By obscuring the internal logic, data structures, and execution flow of an application, preventive obfuscation makes it substantially more difficult for attackers to analyze or tamper with the software. This method is especially effective in deterring reverse engineering and ensuring that even if security breaches occur, the essential elements of the software remain protected.
Benefits of Using Code Obfuscation
Protection Against Reverse Engineering
Obfuscation serves as a crucial defense mechanism against reverse engineering by complicating the readability and comprehensibility of software code. By transforming straightforward code into a convoluted and challenging puzzle, obfuscation techniques like altering control flows, encrypting data strings, and rearranging code structures significantly hinder the ability of attackers to dissect and understand the underlying functionality of the software. This protection ensures that proprietary algorithms, business logic, and sensitive data remain secure from competitors, cybercriminals, and other unauthorized entities seeking to replicate or exploit the software.
Securing Intellectual Property
Obfuscation plays a key role in protecting the intellectual assets of software by masking the source code that embodies valuable proprietary techniques and innovations. This method prevents competitors and malicious entities from easily accessing or replicating the unique aspects of software, such as algorithms, design choices, and specialized processes. By embedding complexity into the code’s structure and execution paths, obfuscation ensures that the intellectual property remains inaccessible and difficult to duplicate, thus safeguarding the company’s competitive advantage and ongoing innovation efforts.
Improve Code Efficiency
While obfuscation is primarily used for security purposes, it can also indirectly lead to improved code efficiency in certain contexts. By restructuring and minimizing code paths through techniques like dead code elimination and optimizing control flows, obfuscation can reduce the code footprint and potentially decrease the load on processors. This streamlining process might result in faster execution times and lower memory usage, particularly in large applications where excess code can be trimmed without affecting functionality. Hence, while its primary goal is to secure code, obfuscation can also contribute to more efficient application performance under specific circumstances.
The Process of Code Obfuscation
Manual Obfuscation
Manual Obfuscation is a technique in the process of code obfuscation where developers intentionally alter the source code by hand to make it more difficult to understand and reverse engineer. This practice involves renaming variables and functions to non-descriptive names, restructuring logical constructs, and inserting misleading comments or removing documentation. Unlike automated tools that apply obfuscation patterns systematically, manual obfuscation allows for more nuanced and creative approaches that can specifically target the most sensitive areas of the codebase. However, it requires a deep understanding of the code and can be time-consuming, making it less scalable for larger projects. Manual obfuscation is particularly useful in tailoring the obfuscation to the specific needs and security concerns of the application.
Automated Obfuscation
Automated obfuscation refers to the use of software tools to obscure source code automatically and systematically. These tools apply a variety of obfuscation techniques such as renaming symbols, encrypting strings, and rearranging code blocks at a scale and speed unachievable by manual methods. Automated obfuscation tools are designed to integrate seamlessly into the build process, ensuring that the obfuscation is consistently applied each time the code is compiled. This not only saves significant time and effort but also helps maintain a consistent level of security across all parts of the application. Automated obfuscation is particularly valuable in large-scale projects where maintaining manual obfuscation practices would be impractical and resource-intensive.
Limitations of Code Obfuscation
While code obfuscation is effective in increasing the difficulty of reverse engineering software, it is not an infallible security solution. One of the primary limitations is that obfuscation does not eliminate vulnerabilities within the code itself; it merely conceals them from immediate view. Skilled attackers with enough time and resources can eventually decipher obfuscated code, especially with the aid of sophisticated de-obfuscation tools and techniques. Additionally, obfuscation can sometimes lead to performance degradation, as the additional complexity introduced can increase the execution time and resource consumption of the application. Moreover, obfuscation can complicate the debugging and maintenance of the software, as the readability and understandability of the code are significantly reduced. These factors make it essential to use obfuscation as part of a broader security strategy, complemented by other defensive measures.
Code Obfuscation in Different Programming Languages
Different languages can be obfuscated to different degrees and require different levels of obfuscation to be truly secure. Languages that compile to an intermediate format , for example, retain a significant amount of metadata which, if not obfuscated, can be reverse engineered easily with off-the-shelf hacking tools. A complete description of the ways in which different languages can and should be obfuscated, click here.
Popular Code Obfuscation Tools
- Dotfuscator: Specifically designed for .NET applications, Dotfuscator offers comprehensive protection by obfuscating code, renaming identifiers, and encrypting strings. It also provides additional security features like tamper detection and expiration to further safeguard applications.
- Obfuscator-LLVM: This tool is an extension of the LLVM compiler designed to add obfuscation capabilities to projects compiled through LLVM. It supports various obfuscation techniques such as control flow flattening and instruction substitution, catering to C and C++ applications.
- JavaScript Obfuscator Tool: Targeting JavaScript, this tool provides obfuscation by transforming the code into a hard-to-understand format using various techniques such as variable renaming, string encryption, and function scrambling. It’s particularly useful for protecting web application scripts from being easily tampered with or copied.
- Xamarin Obfuscator: Aimed at applications developed using the Xamarin framework, this tool helps protect code across different mobile platforms, including iOS and Android. It applies multiple obfuscation methods to manage the specific needs of mobile application security.
These open source tools serve as valuable assets in a developer’s toolkit to help protect intellectual property and enhance the security posture of their applications.
If you are looking for the best obfuscation tools, we’d of course have to recommend our very own Digital.ai Application Security for Mobile, Web, or Desktop applications.
Advancements in Obfuscation Techniques
Here’s an overview of some of the most recent advancements in obfuscation techniques, highlighting the innovative strides being made in this field:
Confidential Computing
One of the cutting-edge advancements in obfuscation is the integration of confidential computing, which allows computations to be performed on encrypted data without needing to decrypt it first. This technique is particularly promising for cloud computing and data privacy, as it enables secure processing while maintaining the confidentiality of the data.
Multi-layered Obfuscation
Developers are now using multi-layered approaches to obfuscation, which apply several different obfuscation techniques at various stages of the software development process. This layered strategy enhances security by making it exponentially harder for attackers to peel back each obfuscated layer.
AI-driven Obfuscation
Artificial intelligence is being used to automate and optimize the obfuscation process. AI algorithms can analyze the code and determine the most effective obfuscation techniques to apply, based on the specific patterns and vulnerabilities present in the software. This method ensures a highly customized and robust obfuscation.
Opaque Predicate*
Recent research has refined the use of opaque predicates in code obfuscation. These are expressions in the code whose truth value is always known at compile time but appears ambiguous to an attacker. Enhancements in generating more complex opaque predicates make the de-obfuscation process more difficult and time-consuming.
Quantum Computing Resistance
As quantum computing advances, researchers are developing obfuscation techniques that can withstand attacks from quantum computers, which could potentially break many of the cryptographic methods currently in use. This involves designing algorithms that are resistant to both classical and quantum decryption methods.
Role of AI in Code Obfuscation
Artificial Intelligence is revolutionizing the field of code obfuscation by introducing smarter, more adaptive techniques that enhance the security and efficiency of software protection measures. Here are some key roles AI plays in this area:
- Automated Obfuscation Decision-Making: AI can analyze a codebase to identify critical segments that would benefit most from obfuscation, thereby optimizing the application of obfuscation techniques. By learning from previous obfuscation outcomes, AI algorithms can predict which methods will be most effective for different types of code, making the process more targeted and efficient.
- Customization and Adaptability: AI-driven tools can tailor obfuscation techniques to the specific architecture and threat model of an application. This personalized approach ensures that obfuscation is not only harder to reverse but also does not unduly affect the performance or functionality of the application.
- Enhanced Complexity and Variability: AI can generate highly complex obfuscation patterns that are more difficult for attackers to analyze or predict. By introducing variability and non-deterministic elements into the obfuscation process, AI makes the reverse engineering process significantly more challenging and time-consuming.
- Dynamic Obfuscation: AI can facilitate dynamic obfuscation where the code modifies its own structure during runtime, based on the execution context or in response to an attack. This live adaptation adds an additional layer of protection, as the obfuscation is not static and changes in response to the environment or threats.
- Integration with Other Security Measures: AI can seamlessly integrate obfuscation with other security techniques, such as encryption and intrusion detection systems. For example, AI can determine the best times and methods for re-obfuscating or decrypting parts of the code based on threat analysis, thereby creating a more robust security posture.