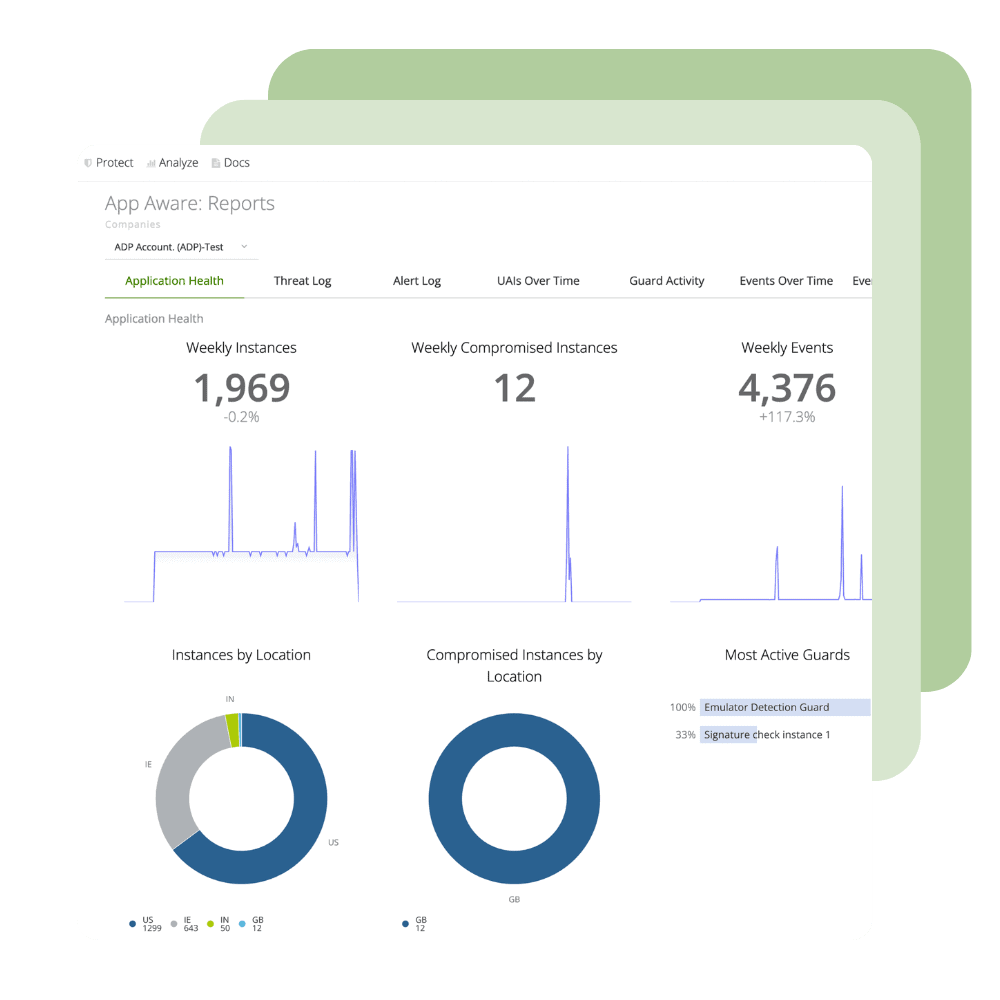
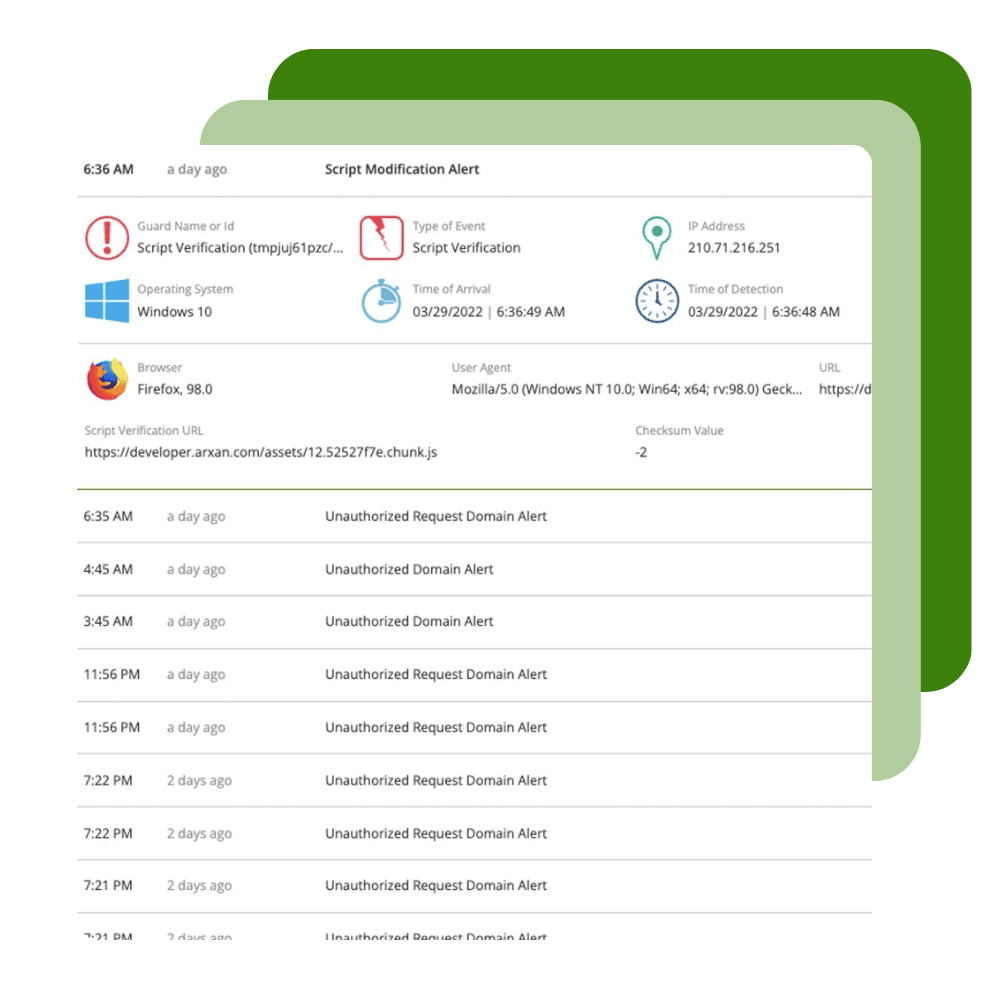
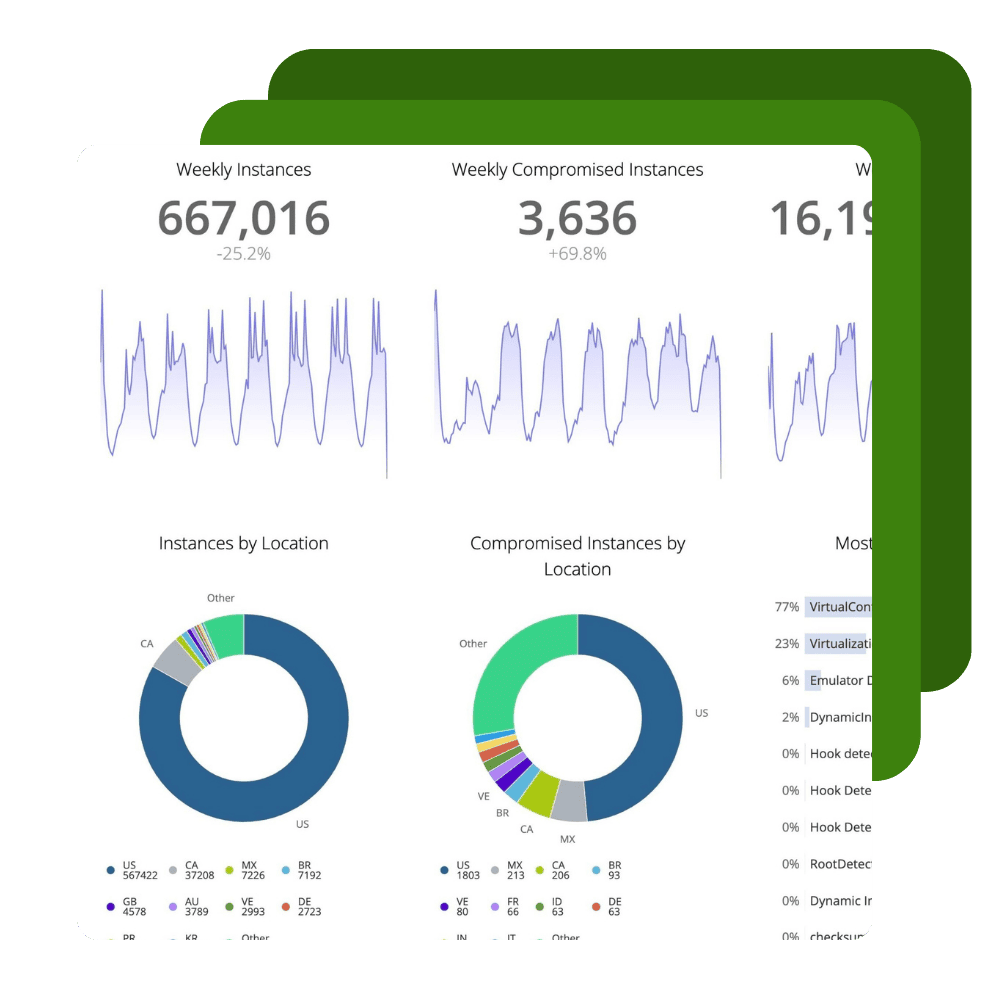
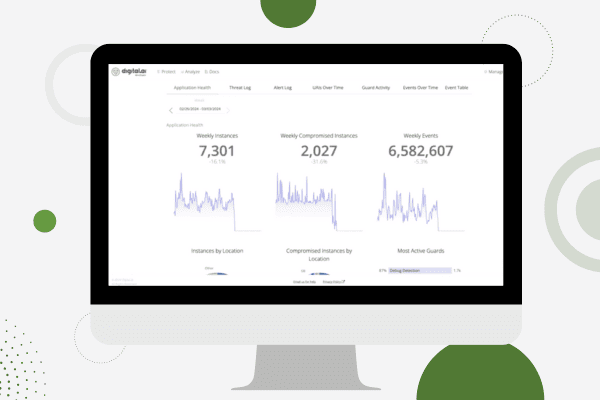
Application Security
Harden applications against reverse engineering attempts, monitor threats to applications, and build runtime application self protection (RASP) into the apps you make and give to your customers.
Protect and Monitor
Ignite your DevSecOps practice by inserting security into your apps at the build phase. Harden your application against reverse engineering, build the ability to monitor threats to your apps in production directly into your SDLC, and create apps that have the ability to automatically react to threats to apps through Runtime Application Self Protection (RASP).
Build Secure Software to Prevent Reverse Engineering
Capabilities
The 2023 Application Threat Report Is Out!

See Digital.ai Application Security in Action
We have helped thousands of enterprises protect, monitor and react to attacks on the apps they make and give to their customers. Contact us to learn more.