App Management
Enterprise mobile app management (MAM) enables IT to balance the unique needs of IT and remote users.
Digital.ai App Management MAM simplifies the management and deployment of apps to any mobile device.
Get started with Digital.ai App Management
The leading enterprise-class MAM® and security platform
Free demo
Connect with our MAM mobile BYOD security experts and listen to an in-depth discussion on the mobile security landscape and view a product demonstration.
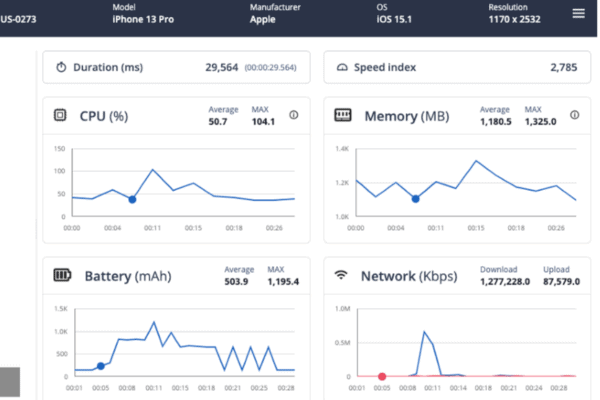
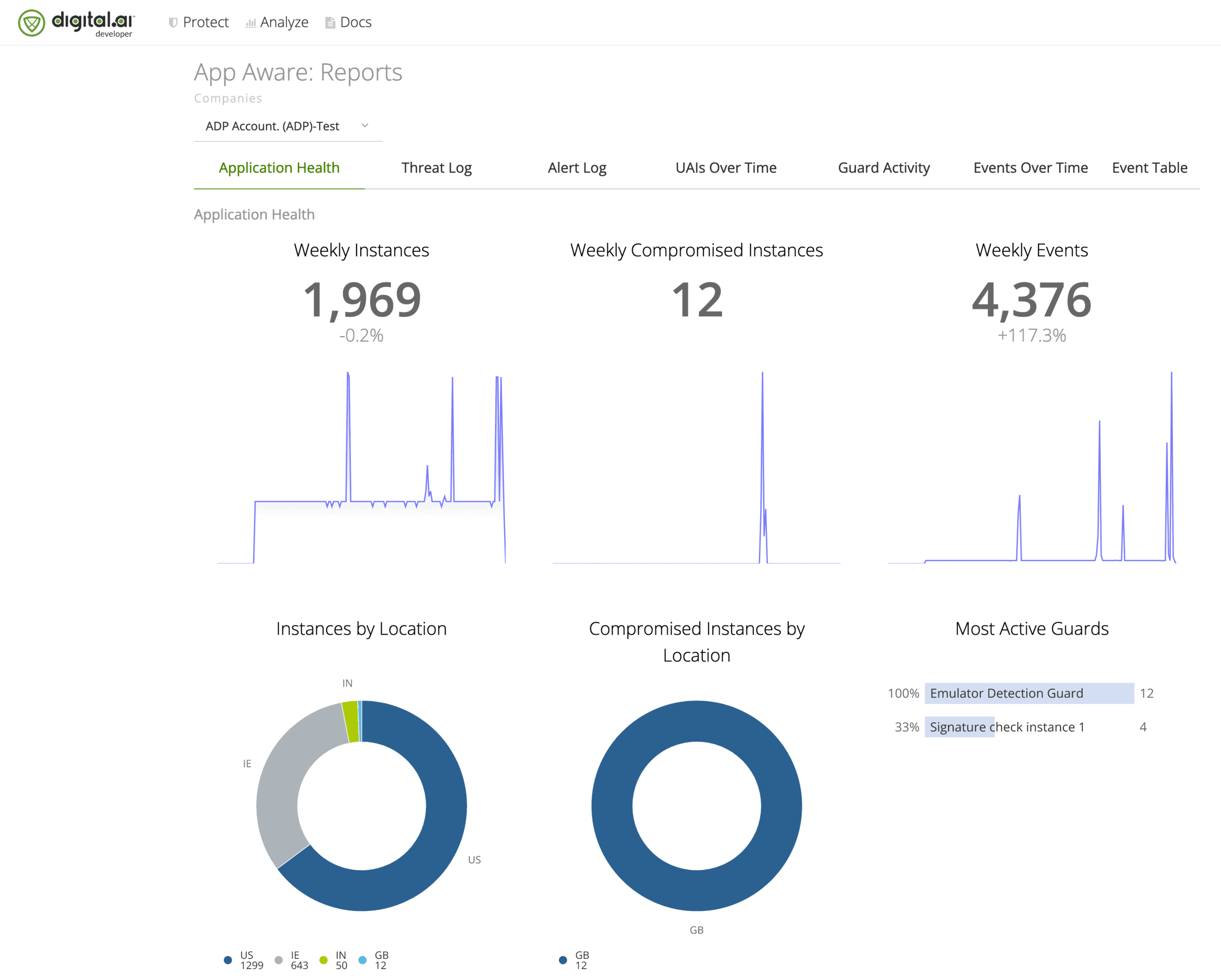
- Tour the Digital.ai App Management platform console and witness the powerful features.
- Receive guidance on enterprise app store capabilities and the values of internal app-store testing.
- View the 5-minute video on Digital.ai App Management MAM and how to support the burgeoning mobile workforce teams.
Definitive Guide to MAM
Best practices for driving secure app adoption and managing the complete mobile app lifecycle.
- Enterprise "apps that matter"
- Mobile-enabling the distributed enterprise
- Limitations of legacy mobile management
Digital.ai App Management Demo
Related Products

App Management
(Formerly Apperian)
Want to learn more about how Application Security will benefit your organization?